Firewall rules (Investigation, Trial and even more errors)
Lets start things off with some basic rules for firewall rules.
1. Any is a bad thing you want to remove this from your rules as much as possible and define everything.
2. lock down your rules to specific IP's even if its only one way. so even if your opening up a port it only to one thing and it should be expecting that traffic.
3. As above, but with ports you don't want more ports open than you need to get your communication working.
4. Alias's are your friend it means if you have multiple rules that use the same alias you can change them all at once
Now with the "rules" done we need to set up some basic rules on the VLAN'd Pf-sense firewall we set up earlier, As right now its operating in white list mode and blocking everything that is not defined in its rules. Which as its has no rules is everything.
In this post we will set up some basic rules as well as some investigation techniques to set up internet rules. I will have a separate post that i will keep updated with other rules that i have found, As even if ports for applications and services are documented sometimes there are ports missed out.
Setting Up Firewall rules
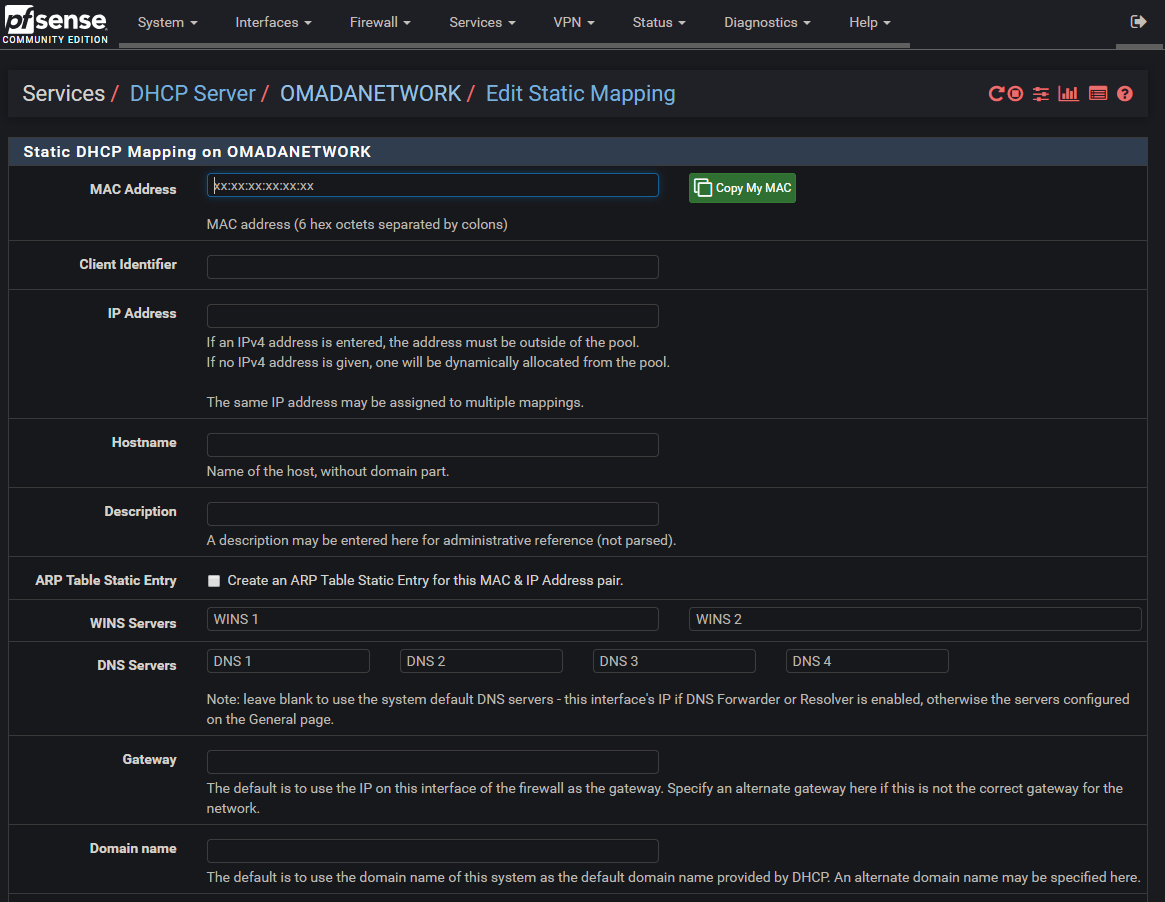
Lets start with setting up basic rules. Now if you have been following along you may have lost connectivity to your PF-Sense router, However there is a fix. Connect your computer directly to your routers LAN port and you should regain the ability to connect. first thing we need to do after you log in is set a static IP to your computer in its VLAN so we can create a rule to give it access to the router. This is done by going to Services > DHCP server. You will see a name for every one of your VLANS as you can see i have a few.
now scroll down to the bottom and you will see "DHCP Static Mappings for this Interface" and under that an add button. slick on that and it will open a new page.
The most important part of this is MAC and IP the rest can be left blank, But for future reference you can assign specific DHCP settings per Computer / Device if you have need.
Set the MAC to that of your main computer and an IP out of the scope of your DHCP, If you set your DHCP to use all of the IP addresses in the list then you will need to set it to use less so its scope would look like 192.168.0.10-254.
once you have your static IP set head over to Firewall > Aliases and you should see this screen...... but with allot less things in it.
Now the reason we are here is to create an alias for our rule, This helps modify the rule in the future as you only need to add/remove IP's/Ports in one place and it will take effect on all rules that reference this alias. Down the bottom of this page is an add button click it to bring up a new page to create your alias.
I always set name and description to the same thing what is important is that it means something to you. Then add the IP address we reserved and a description, I normally use the computer name / device name. Hit save and you back to the alias screen. now its time to create our PF-sense rule by going to Firewall > Rules.
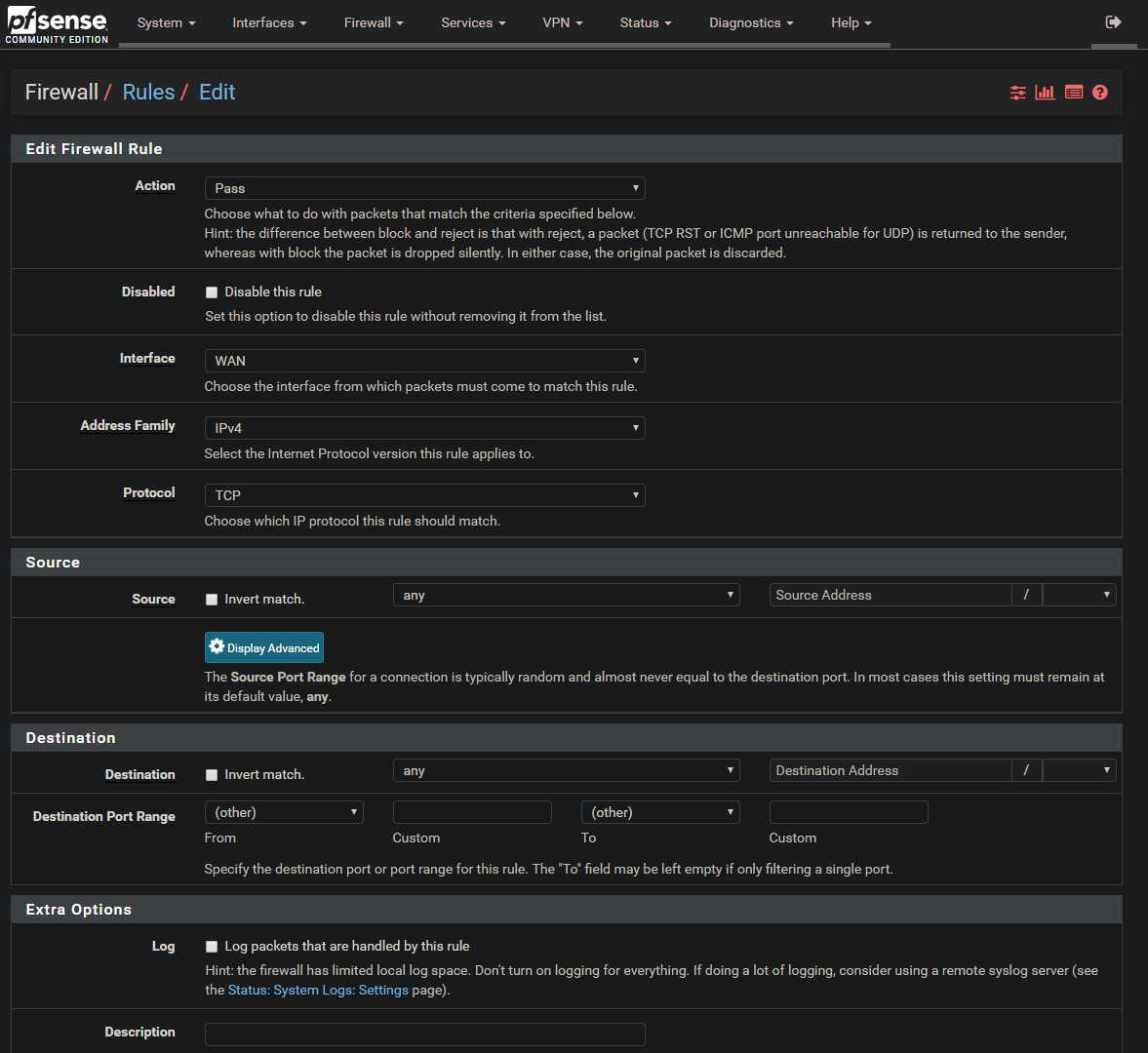
Here we need to select the VLAN we want to create the rule for (The one your computer is going on) then select one of the ADD buttons right now position does not matter but it will later. this will open a new screen.
Here we change the below settings
Protocol: Any
Source: Single Host or Alias
Source Address: start typing the name of the alias we created earlier and it should prompt to autocomplete.
Destination: IP address of your pf-sense routerDescription: something for you to identify this rule.
Now you should be able to connect to your firewall on your VLAN. Once you have you pc re-connected to the switch and the switch connected to the router we can make the default internet rules.
First thing we need to do is head back to Firewall > Alias > Ports. However instead of IP we are going to be creating a port alias. This is important because if we where do do this just using the firewall rules page we would have one rule for every port (i did do this before i found alias's) then select add.this will bring up and almost identical page to the IP address alias page.
For Name and description do the same as before. Now for ports each line you can have 1 port or a range of ports, Fore example ports 500 to 600 would be entered like this 500:600. However we are going off topic here as we are creating the default Internet rules. so add a line for each of the below ports.
Port Description
80 Un-encrypted internet
443 SSL communication
53 DNS
123 NTP Internet time
These are the defaults required for most normal web browsing. Once saved you will want to create another alias for Mail. However you could include this in your default internet rule.
Port Description
995 POP3 Secure
110 POP3 Un-Secure
993 IMAP Secure
143 IMAP Un-Secure
465 SMTP Secure
587 SMTP Submission
25 SMTP Un-Secure
Now we head back to Firewall > Rules. Select your VLAN then add. and change the below settings. If your doing a separate Internet and Mail Rule you will need to do this twice.
Protocol: TCP/UDP
Source: "name of your VLAN" net
Destination : Any (I know i said any is bad earlier however we will mitigate this shortly)
Destination Port Range: Name of your Port / Ports alias
Description: name for your rule
Now click advanced options and scroll down to "Gateway". This should be a drop down menu with default and another name which should have been set up automatically when you set up your router, select this option. this will mitigate the any and force any traffic trying to reach these ports out to the internet. Stopping the traffic from going around your network.
Now hit save. And we are back to the firewall rules screen. now we will want to put the 2 (or 1) rules we created at the bottom of or rule list (This is done by hovering your mouse over the rule the icon will change then you drag it into the new position and hit save at the bottom of the screen). The reason for this being that rules in the list are applied top to bottom. If a rule is found that can apply to that traffic the firewall will not keep looking and apply that rule.
For example we have a server on that you need to send traffic to on port 443 and the rule to allow the traffic between your computer to the server on port 443 is below our default Internet rule. the firewall will hit the default internet rule and as its a positive match it will send that traffic out of the gateway and it will never get to the destination.
Now its time for creating your own rules.
Finding your own rules
Some of this is a bit of trial and error. Say you have a application that you install, It has an internet component and that is not working because its using non standard ports for communicating with the internet. First thing that needs to be done is we need to create a rule, this rule will allow any traffic to any location (its only to be enabled for troubleshooting)
Head to Firewall > Rules select your VLAN and select add and add the below settings.
Protocol: Any
Source: Any
Destination: Any
Log: Tick (this will allow us to see the traffic that passes because of this rule)
Description: Debug
Hit save and you will be at the rules screen. Move this rule to the very bottom as we are running under the assumption the traffic is being blocked because its not in the traffic white-list yet. There is another option but we will go over this later.
Now our rule is in place try your application again (It "Should" work now), Make a note of the time. Now begins the process of finding out why its working, Head over to Status > System Logs and select firewall from the top bar.
On the same bar that has "Status / System Logs / Firewall / Normal View" there is a symbol that looks like a funnel click this and the filter menu will appear. Enter the below
Source IP: put the IP of your computer
PASS: Tick
Then hit apply. This should show you all the traffic that passed because of our logged any rule. Remember how i told you to make note of the time when you used your application earlier, We are now going look at that time in the logs. You should find some ports that where allowed by the rule during that time as well as protocol used. (you could also be ultra secure and take note of the IP addresses, However during this age of load balancing you may have to collect a fair few IP's before you can get your rule working reliably)
Now comes the trial and error. We need to start building a rule start by creating a port alias for the ports you discovered i recommend creating one set for TCP and one for UDP. Once you have that alias created create a rule like the Internet rules we created earlier where instead of the internet alias we use the alias we just created. now place this rule above the basic internet rules. Last step to see if we managed to get all the ports is to disable our any rule this is one by clicking the round symbol in the actions part of the rule.
Now try your application again if it works brilliant! however its most likely not going to. Re-enable your any rule and try again, its possible some of your ports are port ranges so you will need to change them as noted earlier. Some company's have documentation to help with this process and can be correctly documented, However i recently found when creating a rule for iTunes WIFI Sync that a port range it was using for this purpose was documented as being used for XSAN.
Wild tangent over, now that you have you rule working after adjusting for all the ports used during that time. You need to sanity check your rule to make sure you have not erroneously added some ports. So go through your alias remove a port (keep a note of it somewhere) entry and try your application again. If it does not work re-add the port, if it does then it means its possible that your computer was communicating to that port for some other reason (windows telemetry?) keep going through and when your finished you will have your new internet rule!
I will go through certain IOT and other home network device firewall rules in the next article.